Remote Access Portal (on-cloud) Installation
The following steps should be read carefully to install the Remote Access Portal on the regarding machine successfully:
Check the Secure Reboot Enabled before the installation by running mokutil --sb-state command.
If the secure reboot is enabled, it might cause an error during the wireguard installation.
Please disable it to continue the installation!
The user must allow the necessary ports on the Remote Access Portal environment.
sudo firewall-cmd --add-port=443/tcp --permanent
sudo firewall-cmd --add-port=51820/udp --permanent
sudo firewall-cmd --add-port=7777/tcp --permanent
sudo firewall-cmd --add-port=7777/udp --permanent
sudo firewall-cmd --reload
- Download the Remote Access Portal installation script on the machine that is used for the Remote Access Portal. The support team can provide the installation script. After downloading the script, unzip the installation script on the machine. The user can use the unzip command to extract the files from the installation script file.
- unzip RAP-MTC-CLOUD-1.1.0.zip

In case bash: unzip: command not found error is shown, the unzip should be installed via sudo dnf install -y unzip command.
If somehow the user needs to start the script again (maybe, because of the wrong input or missing file, etc…), please remove all installation files except for the compressed Remote Access Portal installation script file and unzip the compressed installation script file again. After this, you can execute the script.
We highly recommend this method, since the extracted files might be modified after the script execution for the first time, and executing the script with modified files might cause the problematic installation!!!
- Navigate to the cloud directory:
- cd cloud/

- Run the configuration script:
- sh configure.sh

In case you need to set script permissions to execute it, you need to run chmod +x configure.sh command.
You should have root privileges to run this script.
- The installation script should be restarted after the forced reboot. The installation script asks the user either:
- To install MT Outbound Connector on the cloud, or to install MT Inbound Connector, or to install the Remote Access Portal (RAP) module on the cloud. (The Secure Remote Access Connector is installed on-prem utilizing the on-prem installation script (e.g., RAP-MTC-ONPREM-1.1.0.zip))
- To continue with the Remote Access Portal (RAP) installation, the user should select the third option by entering 3 and pressing the Enter key.

- The Remote Access Portal installation script asks the user either:
- For the first-time installation on the cloud, the whole Remote Access Portal system should be configured from scratch; thus, the first option should be selected by entering 1 and pressing the Enter key.

The Remote Access Portal installation script asks for several configuration details:
- The Remote Access Portal hostname,
- The port number for WireGuard service,
- The IP segment of Wireguard, the IP address that will be assigned to the Remote Access Portal environment (cloud) handled by Wireguard,
- The IP address that will be assigned to the Secure Remote Access Connector environment (on-prem) handled by Wireguard,
- A public key is generated by the Secure Remote Access Connector’s script.
After filling in every piece of information, the user should press y to continue. However, if the user fails to fill in every piece of information successfully (either missing or incorrect information), the user can press n to reenter the information.
The example values:
https://rap.company.com : (Remote Access Portal hostname)
51820 : (Port Number)
10.0.0.0/29: (IP segment)
10.0.0.1 : (Wireguard IP address assigned to the cloud’s side)
10.0.0.2 : (Wireguard IP address assigned to the RAP connector’s side)
UBuRQ39N30NN0751JBnXoJ5R8M3uTw8NmAkTGI5bLy4=
(Public Key generated by the RAP connector’s script)

Once the Remote Access Portal installation asks the user to enter the public key, if the user doesn’t know the public key generated by the Secure Remote Access Connector’s script yet, the user can set the temporary public key for now.
(e.g., UBuRQ39N30NN0751JBnXoJ5R8M3uTw8NmAkTGI5bLy4=)
But please do not forget to set the public key by using the Remote Access Portal’s script, after the Secure Remote Access Connector’s script generates a public key.
At the end of the Remote Access Portal’s script, the public key generated by this script is ready to use on the Secure Remote Access Connector (on-prem) environment.
(e.g., H7THXCLy28P4pEn/ya2fJ0NgUgIWsV40NMBRyiz3iRI=)

Please do not forget to add this info on the Secure Remote Access Connector environment by using Secure Remote Access Connector’s script.
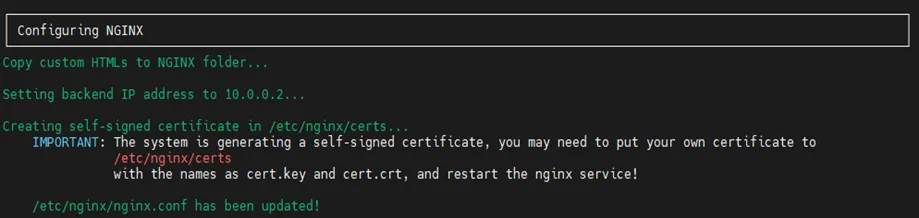
The last step here is to change the self-signed certificate and generic RSA private key with the user’s own certificate and RSA private key. The user should remove the self-signed certificate and generic RSA private key on the /etc/nginx/certs directory. After this, the user should add the user’s AWS certificate and RSA private key with the same names. Lastly, the user should restart the nginx service by using sudo systemctl restart nginx.service command.
Once the Remote Access Portal System has been fully installed, only one configuration is missing here regarding the public key that would be generated by the Secure Remote Access Connector’s script. If the user executes the Secure Remote Access Connector’s script on-premise, it generates a public key which would be used in the Remote Access Portal here, thus now this option can configure the secure tunnel configuration file with the generated public key from Secure Remote Access Connector’s side.
The user should select the second option by entering 2 and pressing the enter key.

Set the public key data of the secure tunnel configuration file with a public key generated by the RAP connector’s script
(e.g., nM8QW+q8tpC6nMNEzIzUtNxNuVePGDPvYF6rFHYBdmU=)
